This post provides steps needed to enable and make use of TOTP two-factor authentication in the Zato Dashboard - the method is compatible with the most popular apps such as Google Authenticator, Authy or FreeOTP.
The functionality is slated for release in Zato 3.1 and, currently, it is available via Zato source installation.
We start by letting web-admin know that it is to require TOTP security codes from users. This is a global flag for all users.
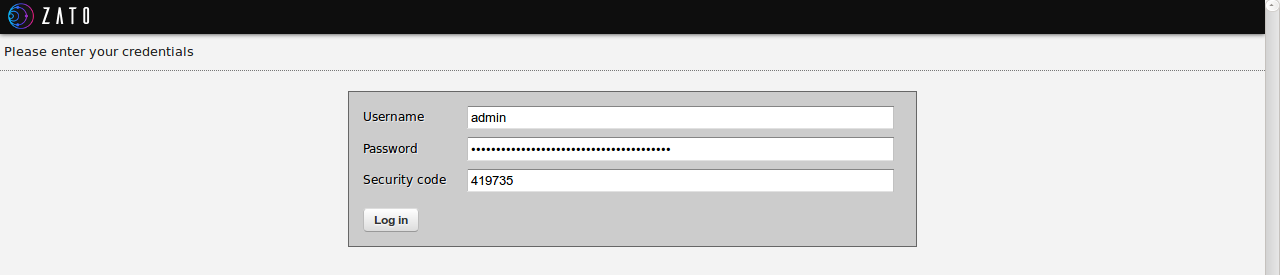
Now that the two-factor authentication with TOTP is enabled, we need the initial TOTP key for each user, otherwise they will not be able to log in at all.
Command line can be used to reset such keys for any user - in this case the process of resetting a key will amount to setting the initial one, as in the sample below that resets the key for a web-admin user called admin:
Such a key can now be transferred to an app of choice to generate time-based security codes that web-admin will require.
The app that the key was saved to will now present security codes needed for logging in.
Each such key is valid for at most 30 seconds - in this way a potential attacker will have to take two factors into account, one is your password and the other is getting access to your app and the associated TOTP secret key. Replay attacks are not particularly feasible against such codes because they will change frequently.
As always, even without TOTP, you should also make sure you rate-limit login attempts to web-admin by configuring your frontend load-balancer, or proxy, accordingly. With TOTP, since the codes are relatively short, it would be possible for an attacker to check them all very quickly so this kind of rate-limiting is of double importance.
Having logged in, it is possible to generate secret keys directly in web-admin too. This option will also output QR codes to transfer the code to mobile devices simply by scanning the resulting QR code.
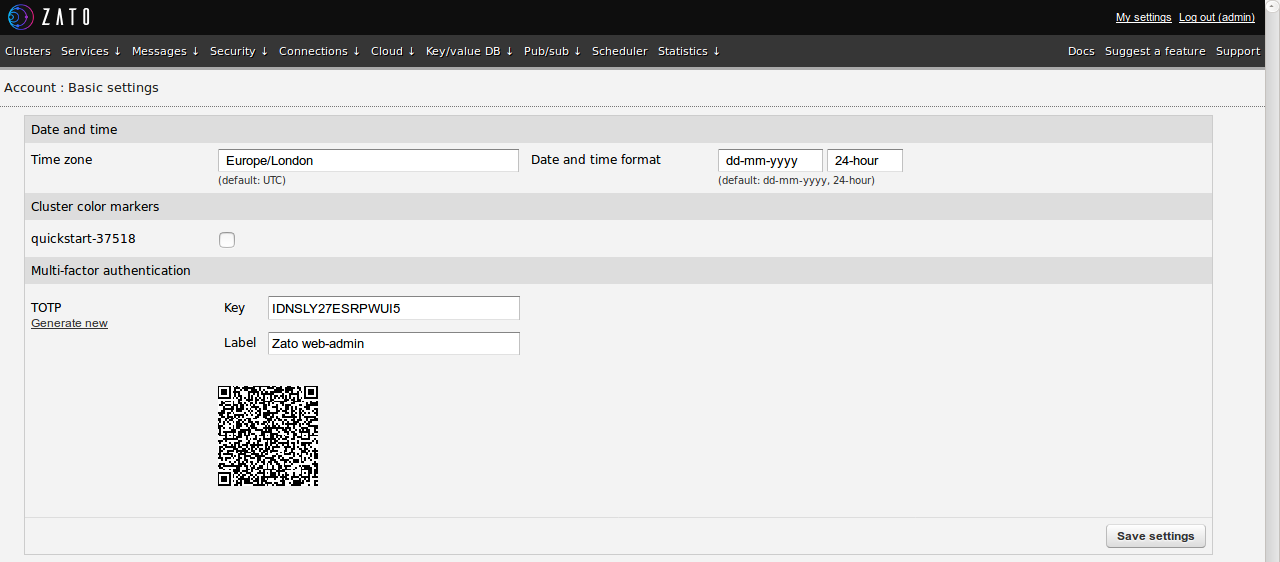
That is all - everything is set up and two-factor authentication will be enforced each time anyone logs in. TOTP is easy to configure and use so it is recommended to enable it as an additional security layer.