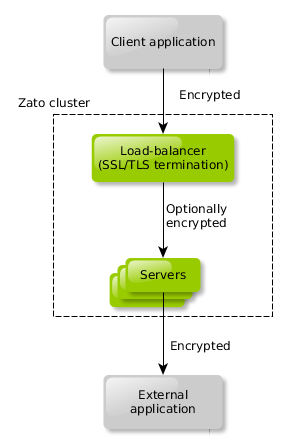
SSL/TLS traffic from a load-balancer to servers
Key features:
- A cluster's HAProxy-based load-balancer can connect to servers using an encrypted SSL/TLS link
- Servers can be configured to require a client certificate from the load-balancer
- Connections from the load-balancer to servers can be encrypted even if connections from client applications to the load-balancer are not
Tasks described in this chapter
- Configuring a load-balancer and servers to use use SSL/TLS without client certificates
- Configuring a load-balancer and servers to use use SSL/TLS with client certificates
SSL/TLS from a load-balancer to servers - no client certificates
- For each server in a cluster, open server.conf and set
crypto.use_tlsto True, so it reads as below. After changing the file, restart the server.
- In Dashboard, open the load-balancer's configuration in source code view
- Find lines referring to servers - contained within the ZATO begin backend bck_http_plain block, such as below. Note that the example shown splits a long line into several ones but the line must be kept long without newlines:
server http_plain--server1 127.0.0.1:17010 \
check inter 2s rise 2 fall 2 \
# ZATO backend bck_http_plain:server--server1
- Add TLS-related configuration, including a path to CA certificates in ca-file which points to CA(s) the server certificates are signed off by, using the example below as a template. Again, all pieces should be placed on one line which has been broken out into multiple ones for clarity:
server http_plain--server1 127.0.0.1:17010 \
check inter 2s rise 2 fall 2 \
ssl verify required \
ca-file /path/to/ca.cert.pem \
# ZATO backend bck_http_plain:server--server1
- Validate and save the load-balancer's configuration
SSL/TLS from a load-balancer to servers - with client certificates
- For each server in a cluster, open server.conf and set
crypto.use_tlsto Truecrypto.tls_client_certsto required, so it reads as below. After changing the file, restart the server.
- In Dashboard, open the load-balancer's configuration in source code view
- Find lines referring to servers - contained within the ZATO begin backend bck_http_plain block, such as below. Note that the example shown splits a long line into several ones but the line must be kept long without newlines:
server http_plain--server1 127.0.0.1:17010 \
check inter 2s rise 2 fall 2 \
# ZATO backend bck_http_plain:server--server1
- Add TLS-related configuration, including a path to CA certificates in
ca-filewhich points to CA(s) the server certificates are signed off by, andcrtcontaining the load-balancer's private key and certificate, using the example below as a template. Again, all pieces should be placed on one line which has been broken out into multiple ones for clarity:
server http_plain--server1 127.0.0.1:17010 \
check inter 2s rise 2 fall 2 \
ssl verify required \
ca-file /path/to/ca.cert.pem \
crt /path/to/key-cert.pem \
# ZATO backend bck_http_plain:server--server1
- Click "Validate and save" to conclude the procedure